com.ibm.ws.webcontainer.httpsession.SessionInspectServlet servlet for inspecting content of a servlet.The
PortletSession object is based on HttpSession, with difference that when you store attribute in the PortletSession in PORTLET_SCOPE , the portal server will name space that attribute and store it in the HttpSession, You can also set an attribute in the PortletSession using APPLICATION_SCOPE it will be stored in the HttpSession without any name spacing.The side effect of this layering is we can use the same
SessionInspectionServlet for inspecting content of a PortletSession.If you want to use SessionInspectionServlet then you need to make sure that value of
enable-serving-servlets-by-class-name is set to true in your ibm-web-ext.xmi file. By default when you create a portlet this value is set to true(You might to add a step to set enable-serving-servlets-by-class-name to false in your security hardening procedure). You can check this value by going to WebSphere\wp_profile\installedApps\\.ear\Contact.war\WEB-INF\ibm-web-ext.xmi for portlet that is installed on your portal, for the portlets that your running through the RAD just check that value in portlet application inside your workspace.Once you ensure that
enable-serving-servlets-by-class-name is set to true the next step would be to figure out the context path of your portlet .war file. You can do this by looking at ibm-web-ext.xmi file of the portlet that you deploy through RAD
<?xml version="1.0" encoding="UTF-8"?>
<web-ext
xmlns="http://websphere.ibm.com/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://websphere.ibm.com/xml/ns/javaee
http://websphere.ibm.com/xml/ns/javaee/ibm-web-ext_1_0.xsd"
version="1.0">
<reload-interval value="3"/>
<context-root uri=".ActionScopeRequestAttribute" />
<enable-directory-browsing value="true"/>
<enable-file-serving value="true"/>
<enable-reloading value="true"/>
<enable-serving-servlets-by-class-name value="true" />
</web-ext>
Value of uri attribute in
context-root element defines the context-root of your web application.If your portlet is installed using Portal admin console then you will have to look inside the application.xml in the
WebSphere\wp_profile\installedApps\\.ear\META-INF folder
<?xml version="1.0" encoding="UTF-8"?><application id="Application_ID" version="5"
xmlns="http://java.sun.com/xml/ns/javaee" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://java.sun.com/xml/ns/javaee
http://java.sun.com/xml/ns/javaee/application_5.xsd">
<display-name>Contact_war</display-name>
<module>
<web>
<web-uri>Contact.war</web-uri>
<context-root>/wps/PA_Contact</context-root>
</web>
</module>
</application>
The value of
context-root is used for defining the context-root of your portlet. Once you know the context-root go to http://localhost:10039/context-root/servlet/com.ibm.ws.webcontainer.httpsession.SessionInspectServlet URL for inspecting value of the servlet.In order to test this feature i did create a portlet that sets one session attribute in
PORTLET_SCOPE and other session attribute in APPLICATION_SCOPE, i did hit the portlet so that the values get set in PorteltSession, this is how my code looks like
request.getPortletSession().setAttribute("applicationScopeAttribute",
"testValue",PortletSession.APPLICATION_SCOPE);
request.getPortletSession().setAttribute("portletScopeAttribute",
"testValue",PortletSession.PORTLET_SCOPE);
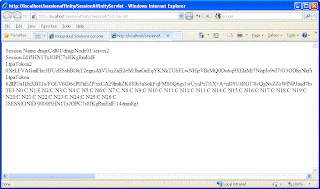
Now in the same browser i did open another tab and when i did hit the SessionInspection servlet this is what i see

As you can see the attribute stored in
APPLICATION_SCOPE gets stored as it is. But for the attribute that is stored in PORTLET_SCOPE the portal server will add javax.portlet.p.<portletwindowid>? prefix