I followed these steps to add LDAP server in my default Federated repository
- First Setup LDAP Server using the instructions in Setting up LDAP Server post. Actually i do have a backup of VMWare with LDAP setup and configured along with WPS 6.1. So if i mess up configuration i can always go to my backup
- Start both server1 and WebSphere_Portal server if they are not already started.
- Open the wp_add_federated_ids.properties file, which is configuration template file that we can use to add IBM Directory server in the federated repository. I changed it to reflect my configuration like this
# *****************************************************************
#
# Licensed Materials - Property of IBM
#
# 5724-L21
#
# Copyright IBM Corp. 2008 All Rights Reserved.
#
# US Government Users Restricted Rights - Use, duplication or
# disclosure restricted by GSA ADP Schedule Contract with
# IBM Corp.
#
# *****************************************************************
###############################################################################
###############################################################################
##
##
## VMM Federated LDAP Properties -
## for creating/updating the LDAP configuration in VMM
## wp-create-ldap
## wp-update-federated-ldap - confirm that federated.ldap.id and federated.ldap.host matches the repository you want to update.
##
##
###############################################################################
###############################################################################
# The id specifies a unique identifier for the repository within the cell
# Characters that are not allowed in normal XML strings ( & < > " ' ) cannot be used in the repository ID.
federated.ldap.id=adminldap
# Specifies the host name of the primary LDAP server. This host name is either an IP address or a domain name service (DNS) name.
federated.ldap.host=localhost
# Specifies the LDAP server port.
federated.ldap.port=389
# Specifies the distinguished name for the application server to use when binding to the LDAP repository.
federated.ldap.bindDN=uid=wpsbind,cn=users,dc=ibm,dc=com
# Specifies the password for the application server to use when binding to the LDAP repository.
federated.ldap.bindPassword=wpsbind
# Specifies the type of LDAP server to which you connect
# Supported values on WAS 6.1: IDS4, IDS51, IDS52, IDS6, SECUREWAY
# Note: If your LDAP server version is not listed, enter the value for the highest listed version of your server
# Supported values on WAS 7: IDS
federated.ldap.ldapServerType=IDS6
# The LDAP base entry.
federated.ldap.baseDN=dc=ibm,dc=com
############################################
#
# LDAP entity types
#
# The supported entity types are
# Group
# default searchFilter =
# default objectClasses = groupOfNames
# default objectClassesForCreate = groupOfNames
# default searchBases =
# PersonAccount
# default searchFilter =
# default objectClasses = inetOrgPerson
# default objectClassesForCreate = inetOrgPerson
# default searchBases =
#
############################################
# Entity type Group
# The search filter that you want to use to search the entity type.
# VMM uses this filter as an addition during search requests in your environment
# The syntax is like a standard LDAP searchfilter like (objectclass=groupOfUniqueNames)
# In general this value can be left blank
federated.ldap.et.group.searchFilter=(objectclass=groupOfUniqueNames)
# One or more object classes (separated by ';') for the entity type.
federated.ldap.et.group.objectClasses=groupOfUniqueNames
# The object class(es) to use when an entity type is created. If the value of this parameter is the same as the objectClass parameter, you do not need to specify this parameter.
federated.ldap.et.group.objectClassesForCreate=
# The search base or bases to use while searching the entity type.
federated.ldap.et.group.searchBases=cn=groups,dc=ibm,dc=com
# Entity type PersonAccount
# The search filter that you want to use to search the entity type.
# VMM uses this filter as an addition during search requests in your environment
# The syntax is like a standard LDAP searchfilter like (objectclass=inetOrgPerson)
# In general this value can be left blank
federated.ldap.et.personaccount.searchFilter=(objectclass=inetOrgPerson)
# One or more object classes (separated by ';') for the entity type.
federated.ldap.et.personaccount.objectClasses=inetOrgPerson
# The object class(es) (separated by ';') to use when an entity type is created. If the value of this parameter is the same as the objectClass parameter, you do not need to specify this parameter.
federated.ldap.et.personaccount.objectClassesForCreate=
# The search base or bases to use while searching the entity type.
federated.ldap.et.personaccount.searchBases=cn=users,dc=ibm,dc=com
#########################
# Group member attributes
#########################
# The name of the LDAP attribute that is used as the group member attribute. For example, member or uniqueMember.
federated.ldap.gm.groupMemberName=uniqueMember
# The group object class that contains the member attribute. For example, groupOfNames or groupOfUnqiueNames.
# If you do not define this parameter, the member attribute applies to all group object classes.
federated.ldap.gm.objectClass=groupOfUniqueNames
# The scope of the member attribute. The valid values for this parameter include the following:
# direct - The member attribute only contains direct members.
# nested - The member attribute that contains the direct members and the nested members.
federated.ldap.gm.scope=direct
# If you create a group without specifying a member, a dummy member will be filled in to avoid creating an exception about missing a mandatory attribute.
federated.ldap.gm.dummyMember=uid=dummy
###############################################################################
##
## Advanced Properties
##
###############################################################################
#
# Group config
#
# The name of the membership attribute. For example, memberOf in an active directory server and ibm-allGroups in IDS.
federated.ldap.gc.name=ibm-allGroups
# Updates the group membership if the member is deleted or renamed. Some LDAP servers, for example, Domino server, do not clean up
# the membership of the user when a user is deleted or renamed. If you choose these LDAP server types in the ldapServerType property,
# the value of this parameter is set to true. Use this parameter to change the value. The default value is false.
federated.ldap.gc.updateGroupMembership=
# The scope of the membership attribute. The valid values for this parameter include the following:
# direct - The membership attribute only contains direct groups.
# nested - The membership attribute that contains the direct groups and the nested groups.
# all - The membership attribute contains direct groups, nested groups, and dynamic members.
# The default value is direct.
federated.ldap.gc.scope=direct
# The implementation class name for the repository adapter.
# The default value is com.ibm.ws.wim.adapter.ldap.LdapAdapter
federated.ldap.adapterClassName=com.ibm.ws.wim.adapter.ldap.LdapAdapter
# Indicates if sorting is supported or not. The default value is false.
federated.ldap.supportSorting=false
# Indicates if transactions are supported or not. The default value is false.
federated.ldap.supportTransactions=false
# Specifies if the external ID is unique. The default value is true.
federated.ldap.isExtIdUnique=true
# Indicates if external names are supported or not. The default value is false.
federated.ldap.supportExternalName=false
# Specifies whether secure socket communication is enabled to the LDAP server.
# When enabled (sslEnabled=true), the Secure Sockets Layer (SSL) settings for LDAP are used.
# The default value is false.
federated.ldap.sslEnabled=false
# Specifies the name of the application server SSL configuration (like mySSLconfig) to be used for SSL enabled LDAP server.
# Application Server SSL config names can be found in Websphere application Server Admin console at Security-SSL certificate and key management
# This property is used to specify a non default SSL configuration if federated.ldap.sslEnabled=true is set
federated.ldap.sslConfiguration=
# Specifies whether to map X.509 certificates into a LDAP directory by exact distinguished name or certificate filter.
# Specify the certificate filter to use the specified filter for the mapping, if client certificate authentication is used
# for portal server.
# Valid values include: EXACT_DN, CERTIFICATE_FILTER
federated.ldap.certificateMapMode=EXACT_DN
# Specifies the filter certificate mapping property for the LDAP filter, if client certificate authentication is used
# for portal server.
# The syntax or structure of this filter is: LDAP attribute=${Client certificate attribute} (for example, uid=${SubjectCN})
# The filter is used to map attributes in the client certificate to entries within the LDAP repository.
federated.ldap.certificateFilter=
# Indicates if paging is supported or not default is false.
federated.ldap.supportPaging=false
# Indicates the authentication method to use. The default value is simple. Valid values include: none or strong.
federated.ldap.authentication=simple
# Indicates the property name used for login. Common values include: uid or cn
federated.ldap.loginProperties=uid
# The LDAP referral. The default value is ignore. Valid values include: ignore, follow, throw, or false.
federated.ldap.referral=ignore
# Controls how aliases are dereferenced. The default value is always. Valid values include:
# always - always deference aliases
# never - never deference aliases
# finding - deference aliases only during name resolution
# searching - deference aliases only after name resolution
federated.ldap.derefAliases=always
# The connection pool. The default value is false.
federated.ldap.connectionPool=false
# The connection timeout measured in seconds. The default value is 0.
federated.ldap.connectTimeout=0
# Indicates the polling interval for testing the primary server availability.
# The value of this parameter is specified in minutes. The default value is 15.
federated.ldap.primaryServerQueryTimeInterval=15
# Indicates to return to the primary LDAP server when it is available. The default value is true.
federated.ldap.returnToPrimaryServer=true
# The value of search page size. This is the number of entries per page. The default is 50.
federated.ldap.searchPageSize=
# The value of the search count limit.
federated.ldap.searchCountLimit=500
# The value of the search time limit measured in miliseconds.
federated.ldap.searchTimeLimit=120000
# Indicates to translate RDN or not. The default value is false.
federated.ldap.translateRDN=false
# The maximum number of context instances that can be maintained concurrently by the context pool.
# The default value is 20.
federated.ldap.cp.maxPoolSize=20
###############################################################################
###############################################################################
##
##
## End - VMM Federated LDAP Properties
##
##
###############################################################################
############################################################################### - Once the wp_add_federated_ids.properties file is setup we need to validate the values entered in the file. So execute this configuration task
./ConfigEngine.sh validate-federated-ldap -DWasPassword=wasadmin -DparentProperties=/software/WebSphere/wp_profile/ConfigEngine/config/helpers/wp_add_federated_ids.properties - If the validation task is successful then execute
wp-create-ldaptask to apply the configuration
./ConfigEngine.sh wp-create-ldap -DWasPassword=wasadmin -DparentProperties=/software/WebSphere/wp_profile/ConfigEngine/config/helpers/wp_add_federated_ids.properties - Once the configuration task is completed successfully, restart the WebSphere_Portal and Server1.
Now you should be able to login into portal using one of the users in LDAP server. Now you can verify your new LDAP repository by executing the
./ConfigEngine.sh wp-query-repository -DWasPassword=wasadmin Configuration task. You should list of repositories like this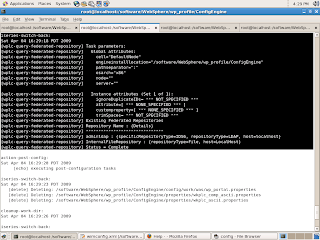
3 comments:
Hi
I am using ApacheDS instead of IDS.
I followed your instructions and set up wpsadmins group with admin user in ApacheDS.
Then executed steps to add the ldap repository.
I got an error during this which said PersonAccount does not exist, although the repository was created.
I then added PersonAccount entity using wp-create-ldap-entitytype.
But when I restart my WAS I get this error, Any ideas / any help will be highly appreciated
[8/27/09 12:37:44:704 EDT] 0000000a UserRegistryI E SECJ0330E: The registry implementation file com.ibm.ws.wim.registry.WIMUserRegistry cannot be loaded because of the following exception java.lang.NullPointerException
at com.ibm.ws.wim.adapter.ldap.LdapConfigManager.setGroupMemberFilter(LdapConfigManager.java:2236)
at com.ibm.ws.wim.adapter.ldap.LdapConfigManager.initialize(LdapConfigManager.java:252)
at com.ibm.ws.wim.adapter.ldap.LdapAdapter.initialize(LdapAdapter.java:167)
at com.ibm.ws.wim.RepositoryManager.initialize(RepositoryManager.java:518)
Rajiv,
I am not sure what could be wrong, do you know if Apache DS is supported as LDAP server. I never seen anyone using that LDAP.
Hi
Was Able to configure ApacheDS with VMM.
It should be added as CUSTOM ldap. And dont run wp-create-ldap-entitytype for PersonAccount entity you should be good with that..appartently running aforementioned task causes problems
Post a Comment